IAM security policies include: 1. Establish clear and concise IAM policies that specify who can access what resources and how they can be used. 2. Use strong authentication and authorization
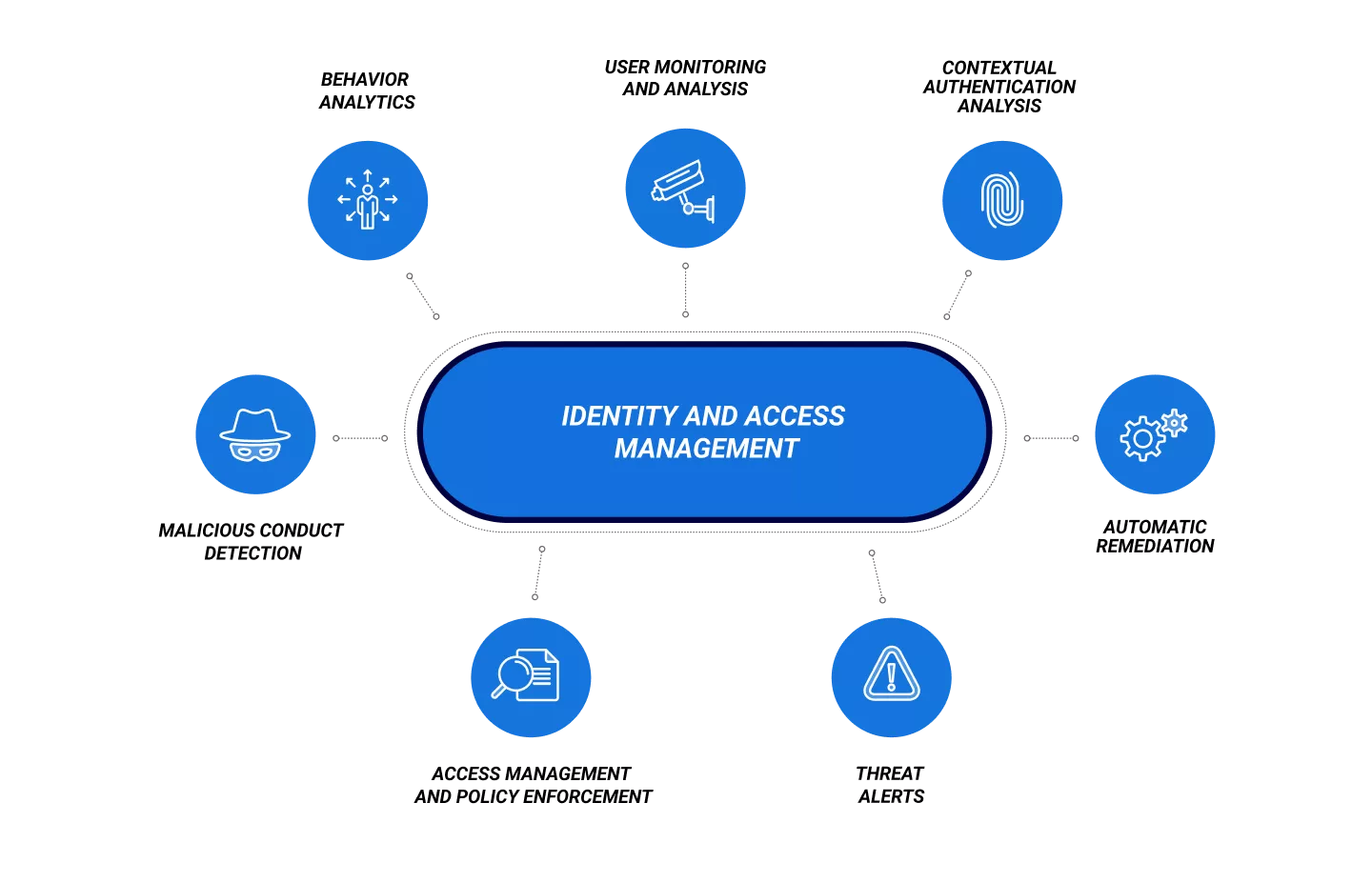
IAM security policies include: 1. Establish clear and concise IAM policies that specify who can access what resources and how they can be used. 2. Use strong authentication and authorization