While the primary goal of cybersecurity practices is to enhance the security of an environment, there are certain practices or misconfigurations that could inadvertently encourage hackers or make the overall
Month: May 2023
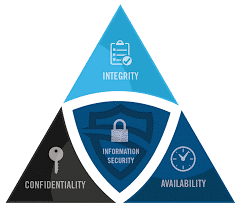
The CIA Triad ModelThe CIA Triad Model
The Cybersecurity CIA triad is a security model that is used to protect information systems. The triad consists of three components: Confidentiality, Integrity, and Availability. Confidentiality ensures that only authorized

Roles of an IAM EngineerRoles of an IAM Engineer
What are some Day to Day activities of an IAM engineer in some organizations?
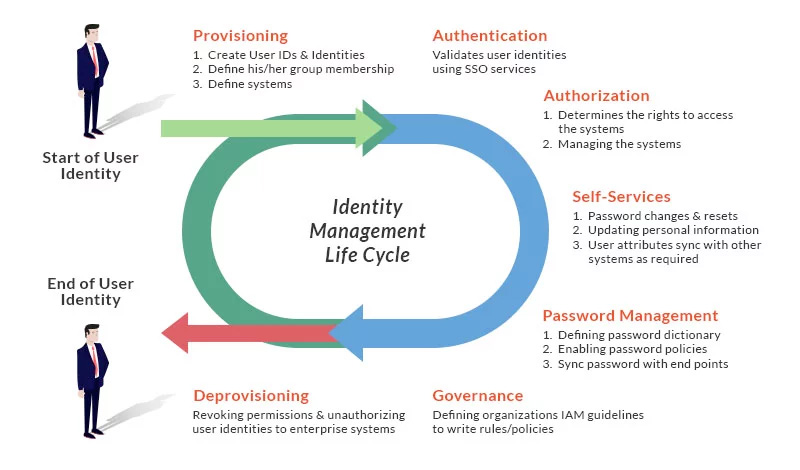
What Are The Phases In The IAM LifecycleWhat Are The Phases In The IAM Lifecycle
The IAM lifecycle consists of four cycles: 1. Provisioning: This is the process of creating and configuring IAM resources such as users, groups, roles, and policies. 2. Governance: This is

5 Key Steps to Securing An Environment5 Key Steps to Securing An Environment
1. Multi-Factor Authentication: Implementing multi-factor authentication (MFA) is a crucial step in securing cloud-based apps. MFA requires users to provide two or more forms of authentication before accessing the app,

Top IT Certifications in 2023Top IT Certifications in 2023
The top IT certifications currently can vary depending on the specific field and technology you are interested in, but here are some of the most popular certifications: These are just

How Do I Get Started With A Career in IT Security?How Do I Get Started With A Career in IT Security?
Getting started in IT security can be a challenging but rewarding career path. Here are some steps to help you get started: Remember that IT security requires a commitment to

